Apple's $3 billion acquisition of Beats caught almost everyone off guard. Not only was the purchase price drastically higher than what Apple typically spends for acquisitions, but Apple's interest in Beats in and of itself was the source of much... -- For more information read the original article here.
Adding to the din of rumors regarding an Apple-branded mobile payments solution, a report on Tuesday claims the Cupertino company is discussing a platform launch partnership with department store giant Nordstrom.
-- For more information read the original article here.
-- For more information read the original article here.
Earlier today, Apple issued a press release stating that an iCloud/Find My iPhone breach had not been responsible for the leak of several private celebrity photos over the weekend, instead pointing towards a "very targeted attack on user names, passwords, and security questions" hackers used to gain access to celebrity accounts.
The company did not divulge specific details on how hackers accessed the iCloud accounts, leading Wired writer Andy Greenberg to investigate the methods that hackers might possibly have used to acquire the stolen media.
Greenberg visited Anon-IB, a popular anonymous image board where some of the celebrity photos first originated, and discovered that hackers openly discuss exploiting software designed for law enforcement and government officials. Called ElcomSoft Phone Password Breaker (EPPB), the software in question lets hackers enter a stolen username and password to obtain a victim's full iPhone/iPad backup.
According to security researcher Jonathan Zdziarski, who spoke to Wired, metadata from some of the leaked photos is in line with the use of the ElcomSoft software and possibly the iBrute software, which exploited a vulnerability in Find My iPhone to allow hackers unlimited attempts to guess a password. Apple has, however, patched the exploit, and has suggested iBrute was not a factor in the attacks.
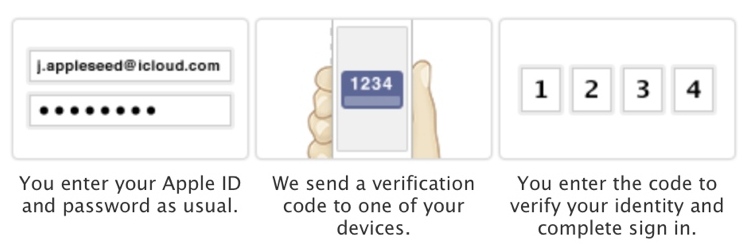
As noted by TechCrunch, using ElcomSoft's software to download an iPhone's backup successfully circumvents two-factor verification as the two-factor authentication system does not cover iCloud backups or Photo Stream.
Two-factor verification can make it much more difficult for hackers to acquire a user's login credentials in the first place, preventing many attacks, but an iCloud backup can be installed with just a user name and a password.
The ElcomSoft software does not require any credentials to buy and while it costs $399, it is also available on bittorrent sites. The vulnerability in iCloud backups has been known for some time, with ElcomSoft's own CEO pointing towards the lack of two-factor authentication for iCloud backups -- For more information read the original article here.
The company did not divulge specific details on how hackers accessed the iCloud accounts, leading Wired writer Andy Greenberg to investigate the methods that hackers might possibly have used to acquire the stolen media.
Greenberg visited Anon-IB, a popular anonymous image board where some of the celebrity photos first originated, and discovered that hackers openly discuss exploiting software designed for law enforcement and government officials. Called ElcomSoft Phone Password Breaker (EPPB), the software in question lets hackers enter a stolen username and password to obtain a victim's full iPhone/iPad backup.
"Use the script to hack her passwd...use eppb to download the backup," wrote one anonymous user on Anon-IB explaining the process to a less-experienced hacker. "Post your wins here ;-)"Acquiring just a user name and password allows hackers access to content on iCloud.com, but with the accompaniment of the ElcomSoft software, a complete backup can reportedly be downloaded into easy-to-access folders filled with the device's contents.
According to security researcher Jonathan Zdziarski, who spoke to Wired, metadata from some of the leaked photos is in line with the use of the ElcomSoft software and possibly the iBrute software, which exploited a vulnerability in Find My iPhone to allow hackers unlimited attempts to guess a password. Apple has, however, patched the exploit, and has suggested iBrute was not a factor in the attacks.
As noted by TechCrunch, using ElcomSoft's software to download an iPhone's backup successfully circumvents two-factor verification as the two-factor authentication system does not cover iCloud backups or Photo Stream.
Two-factor verification can make it much more difficult for hackers to acquire a user's login credentials in the first place, preventing many attacks, but an iCloud backup can be installed with just a user name and a password.

The ElcomSoft software does not require any credentials to buy and while it costs $399, it is also available on bittorrent sites. The vulnerability in iCloud backups has been known for some time, with ElcomSoft's own CEO pointing towards the lack of two-factor authentication for iCloud backups -- For more information read the original article here.
Infected site attracts companies from automotive, aerospace and manufacturing sectors. -- For more information read the original article here.
The Obama administration is looking to a pool of private-sector talent for people willing to bring their professional expertise to new jobs with the government. -- For more information read the original article here.
Google is rebranding its efforts for enterprise. In a blog post heralding the change Chairman Eric Schmidt noted that the business focused offerings from the search engine giant will now be known as Google for Work, with no other changes made to the products other than the name. Encompassed under the new nomenclature are Gmail and Hangouts, plus Google Calendar, Drive, Docs, Sheets, Slides, Groups, News, Play, Sites, and Vault....
-- For more information read the original article here.
-- For more information read the original article here.
Apple has issued a new follow-up statement on this week's celebrity photo leaks via iCloud. "After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet," the company writes. "None of the cases we have investigated has resulted from any breach in any of Apple's systems including iCloud or Find My iPhone. We are continuing to work with law enforcement to help identify the criminals involved."...
-- For more information read the original article here.
-- For more information read the original article here.